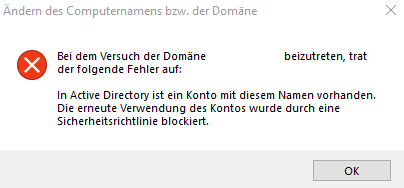
In an Active Directory domain, the problem occurred that no new computers could be added to the Active Directory. The error message when adding the client was as follows:
An account with this name exists in the Active Directory. Re-use of the account has been blocked by a security policy
In the domain, an Identity Manager could be created before the computer is added to the Active Directory (pre-staged) and not only when the computer is added to the AD. In this case, the computer account already exists and was created by a service account of the Identity Manager (in this example, the service account is called "IdentityManager"). With another user account, which is only used for the domain join, an attempt has now been made to add the new client to the Active Directory. Simply put: The computer account of the client is created by userA and userB wants to add the computer to the AD. This results in the error described above.
In this case, a security policy prevents a user from using computer accounts that were created by another user. UserB (DomainJoin) can therefore not customize / reuse the computer account that was created by UserA (IdentityManager).
The error is a feature that is not actually new, but has now occurred in this domain due to the Identity Manager. The corresponding security policy "Domain join hardening changes" has been prepared since October 2022 and adapted with the Windows updates of 13.08.2024.
The following line is logged in the Netsetup.log of the client:
NetpModifyComputerObjectInDs: Account exists and re-use is blocked by policy. Error: 0xaac
Here are all the relevant lines from the log file c:\Windows\debug\Netsetup.log of the client in question:
01/02/2025 13:59:43:058 NetpReadAccountReuseModeFromAD: Got 0 Entries.
01/02/2025 13:59:43:058 Returning NetStatus: 0, ADReuseMode: 0
01/02/2025 13:59:43:058 IsLegacyAccountReuseSetInRegistry: RegQueryValueEx for 'NetJoinLegacyAccountReuse' returned Status: 0x2.
01/02/2025 13:59:43:058 IsLegacyAccountReuseSetInRegistry returning: 'FALSE''.
01/02/2025 13:59:43:074 NetpDsValidateComputerAccountReuseAttempt: returning NtStatus: c0000022, NetStatus: 5
01/02/2025 13:59:43:074 NetpDsValidateComputerAccountReuseAttempt: returning Result: FALSE
01/02/2025 13:59:43:074 NetpCheckIfAccountShouldBeReused: Active Directory Policy check with SAM_DOMAIN_JOIN_POLICY_LEVEL_V2 returned NetStatus:0x5.
01/02/2025 13:59:43:074 NetpCheckIfAccountShouldBeReused:fReuseAllowed: FALSE, NetStatus:0x0
01/02/2025 13:59:43:074 NetpModifyComputerObjectInDs: Account exists and re-use is blocked by policy. Error: 0xaac
01/02/2025 13:59:43:074 NetpProvisionComputerAccount: LDAP creation failed: 0xaac
01/02/2025 13:59:43:074 ldap_unbind status: 0x0
01/02/2025 13:59:43:074 NetpJoinCreatePackagePart: status:0xaac.
01/02/2025 13:59:43:074 NetpJoinDomainOnDs: Function exits with status of: 0xaac
01/02/2025 13:59:43:074 NetpJoinDomainOnDs: status of disconnecting from '\\dc.domain.local': 0x0
01/02/2025 13:59:43:074 NetpResetIDNEncoding: DnsDisableIdnEncoding(RESETALL) on 'domain.local' returned 0x0
01/02/2025 13:59:43:074 NetpJoinDomainOnDs: NetpResetIDNEncoding on 'domain.local': 0x0
01/02/2025 13:59:43:074 NetpDoDomainJoin: status: 0xaac
To resolve the problem with the security policy, a new GPO can be created for the domain controller that allows the reuse of previously created computer accounts.
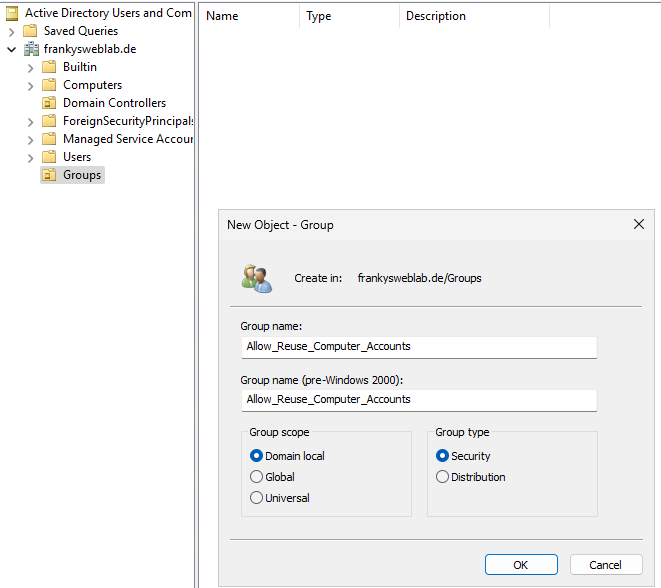
A new group is first required for the group policy; this group is used to authorize the accounts that are allowed to reuse computer accounts. I have named the group "Allow_Reuse_Computer_Accounts":
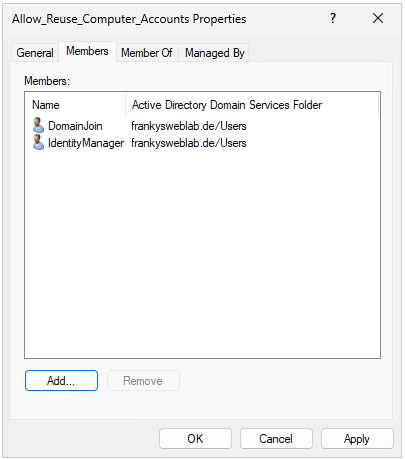
The accounts that create computer accounts and the user accounts that reuse computer accounts, i.e. add clients to the domain, are entered as members of the new group:
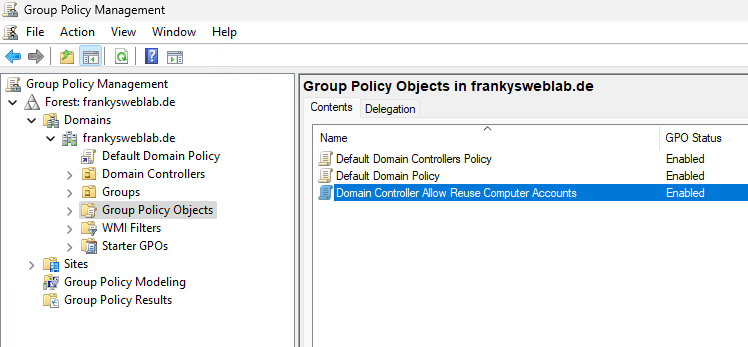
Now a new group policy is created. I have named the new group policy "Domain Controller Allow Reuse Computer Accounts":
The following setting can now be activated in the group policy:
- Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Local Policies -> Security Options -> Domain Controller: Allow Computer account re-use during domain join
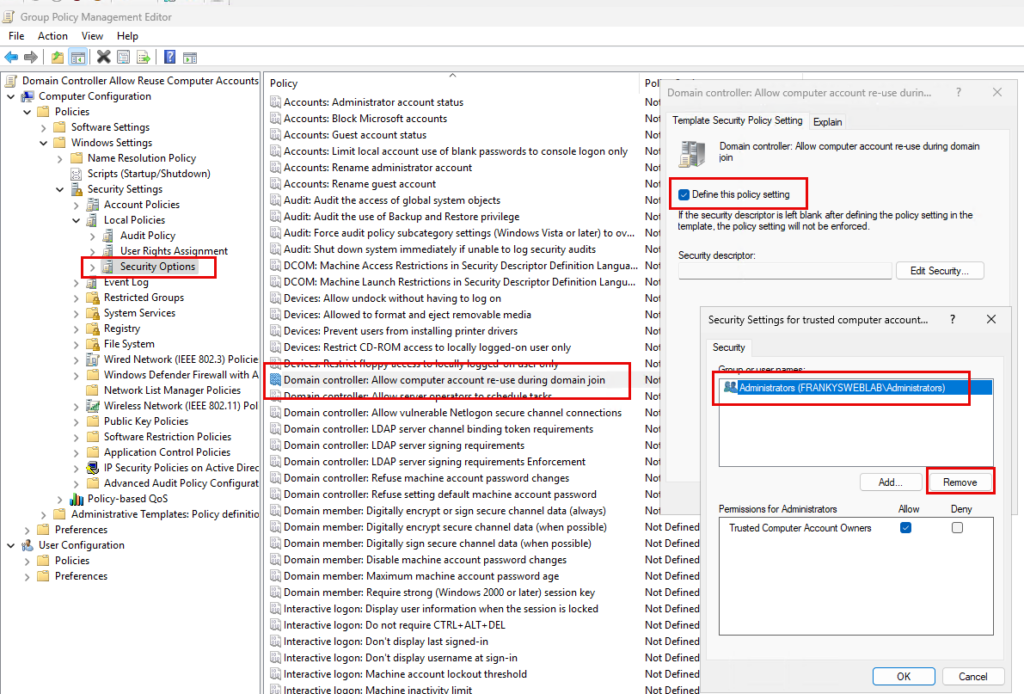
The "Administrators" group is now deleted in the settings and the previously created group is added:
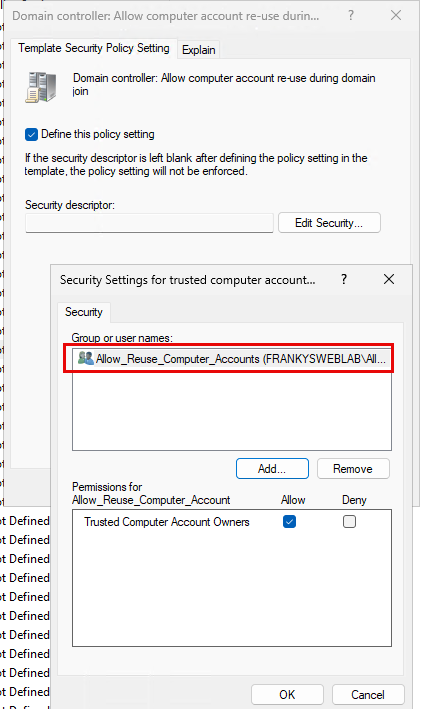
In addition, the new group must be entered for the following setting:
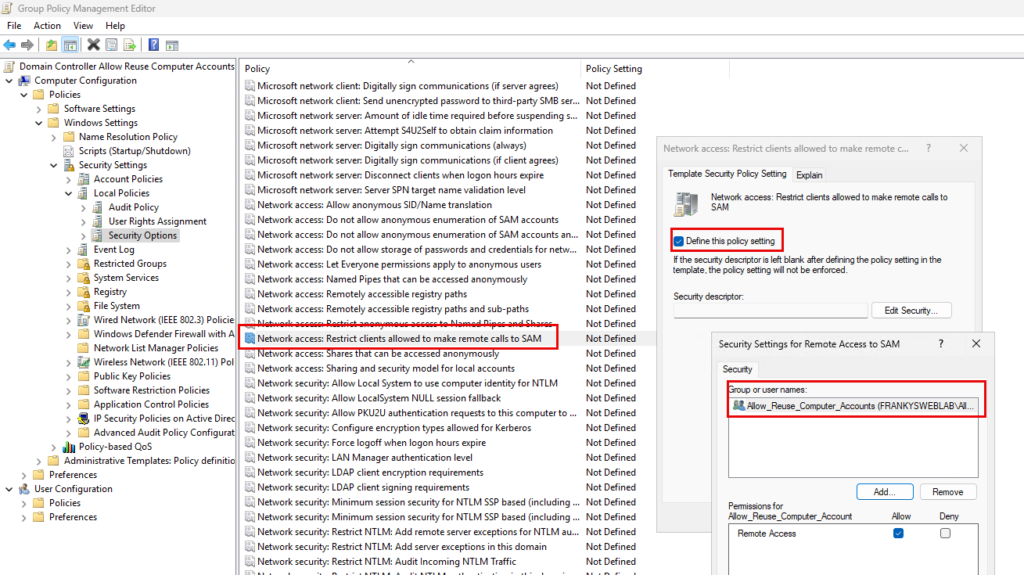
- Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Local Policies -> Security Options -> Network Access: Restricts clients allowed to make calls to SAM
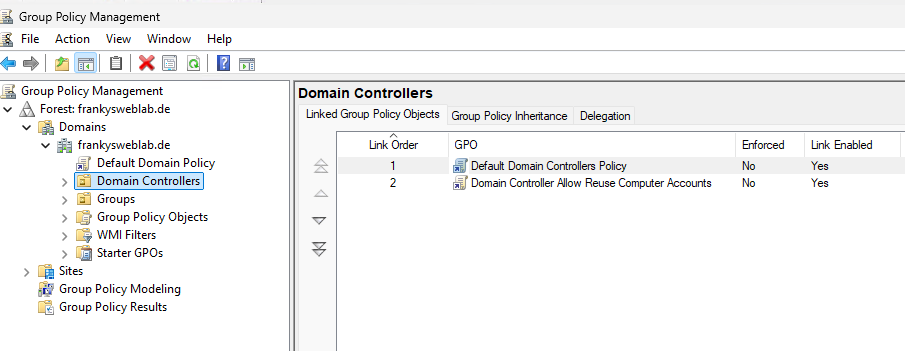
Finally, the new group policy must be linked to the "Domain Controller" organizational unit:
After applying the group policy, the members of the group can reuse computer accounts or add clients to the Active Directory again.
Thanks Franks. Was struggling on this issue for days. Everyone was suggesting editing „Allow Computer account re-use during domain join“, but not „Restricts clients allowed to make calls to SAM“ setting.
As soon relax the SAM calls entry, was able to join the computer to domain.
Thanks again. Cheers.
Funktioniert bei mir leider nicht. Egal was ich mache.
Hallo Frank, vielleicht solltest Du noch erwähnen das der Schritt die Usergruppe in die Einstellung „Network access – Restrict clients allowed to make remote calls to SAM“ hinzuzufügen nur notwendig ist wenn man dort bereits Einschränkungen vorgenommen hat.
Ist diese Einstellung bis dahin noch auf „Not defined“ gestellt, sollte es auch so bleiben.
Siehe auch den KB5020276 Artikel von Microsoft unter Known Issues, Issue 1.
Danke für den Beitrag. Kann man das ganze auch auf lokale Ebene runterbrechen – also in die dortige lokale Gruppenrichtlinie?
Verstehe nicht so ganz, weshalb man Computerkonten wiederverwenden sollte. Wir löschen sie grundsätzlich, bevor wir den gleichen Hostname wiederverwenden.
Es geht nicht nur ums Wiederverwenden, sondern um die Teilung zwischen Konto anlegen und Computer aufnehmen. Hat Franky doch oben gut beschrieben. Nicht immer nur in „klein“ denken. ;)